Southwest Airlines, the fourth largest airline in the US, is seemingly unaffected by the problematic CrowdStrike update that caused millions of computers to BSoD (Blue Screen of Death) because it used Windows 3.1. The CrowdStrike issue disrupted operations globally after a faulty update caused newer computers to freeze and stop working, with many prominent institutions, including airports and almost all US airlines, including United, Delta, and American Airlines, needing to stop flights.
Windows 3.1, launched in 1992, is likely not getting any updates. So, when CrowdStrike pushed the faulty update to all its customers, Southwest wasn’t affected (because it didn’t receive an update to begin with).
The airlines affected by the CrowdStrike update had to ground their fleets because many of their background systems refused to operate. These systems could include pilot and fleet scheduling, maintenance records, ticketing, etc. Thankfully, the lousy update did not affect aircraft systems, ensuring that everything airborne remained safe and were always in control of their pilots.
This software is shit Bob! What should we do Bob?
Well Bob, we should find something compatible with shit!
Bob, I think I got it! I got this other shit software!
Genius Bob! Just Genius! 😎
This… Doesn’t make me feel any better about flying Southwest
because Boeing or why?
Wait till you hear of how much COBOL in industries…
Old programming languages are fine. Hard to maintain though. But they all compile down to machine code at the end of the day.
Old operating systems on the other hand means they are vulnerable to all kinds of exploits that have been discovered in that OS over the past few decades. That’s a much bigger problem.
i think you accedentaly put southwest instead of spirit.
Spirit is already a non starter for me because my legs don’t fit in the seat haha
i don’t think there’s any possible way to feel better about flying southwest
And they can play JezzBall.
windows downfall began when they removed jezzball. prove me wrong.
Maybe don’t pay a company to install a rootkit on your critical infrastructure?
Just open up your critical infrastructure to the public Internet and you’ll get rootkits for free.
So…Battlestar Galactica scenario?
I love such things in Star Wars too.
And not sure whether there’s been a plot play with the Katana fleet (all ships were slaved to the flagship, all crews including that of the flagship caught a virus causing them to go mad and die, and while they were still alive, the fleet jumped in unknown direction ; it was found later and ships reused by sides of the civil war) where its obsolete electronics and software were actually an advantage security-wise.
Though in that universe it seems that interfacing and integrating wildly different systems is more or less a normal thing, since there are lots of planets, lots of races and some things still in operation are few centuries old.
lol
Or, for your consideration, could it perhaps be because they don’t use crowdstrike?
My Linux servers weren’t affected either. I think it’s because of Windows 3.1
My wife shared this with me yesterday, but I didn’t see it:
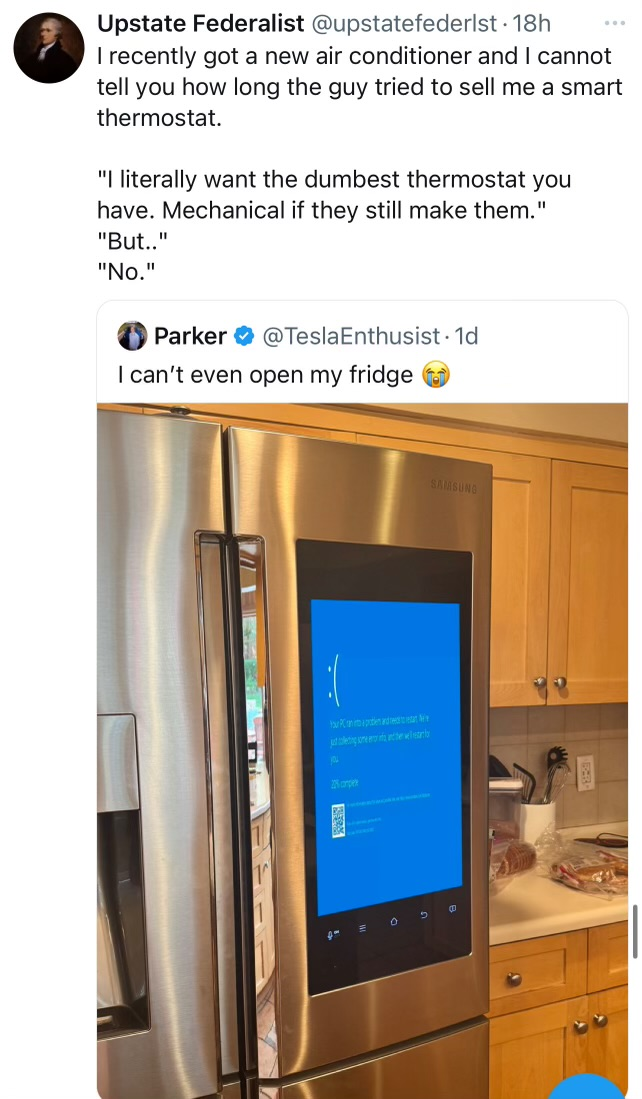
Somebunny is gonna learn those things aren’t windows-based today!
My old thermostat was basically two teaspoons of mercury that would expand and contract with the temperature to short out two leads. They didn’t let me keep it when I got a new one, but I got the dumbest one they had.
I got a new HVAC and smart thermostat about a week ago. After researching, I decided to hook thermostat to wifi and download app. Mostly all the app does is duplicate the same functionality that the thermostat controls have. I find it handy to have a remote control for the thermostat.
OTOH I decided not to hook up a new washing machine to wifi and use app. It duplicated the functionality of the appliance controls also, but there was no point in having remove controls for a washing machine.
The critical thing is that an appliance needs to be fully functional without needing to use wifi and certainly not a phone app.
Just yesterday I had that exact “Tech enthusiast vs tech worker” meme play out. I wanted a timer to control the electrical outlet for an aquarium bubbler. Saleswoman really wanted to sell me this “smart” controller with an app that can program the outlet.
Me:“What happens when the app stops working?”
(saleswoman is frantically flipping the box over for answers)
Her:“…maybe…it keeps the existing timer?”
For only way more time and money, you can buy a zigbee smart plug and a vendor agnostic zigbee hub flashed with FOSS, or you can buy a esp-based board, wire it up with a relay, and flash it with something like esphome.
Sure, it’s way more money and hours of work (cumulatively), but it won’t lose support!
I just bought a bunch of TP Link equipment I knew was compatible and loaded up Home Assistant onto a Raspberry Pi. Best of both worlds
I bought some TP link Kasa plugs and a couple of years later when I wanted some more the Kasa brand was discontinued and replaced by Tapo in Sweden. Tapo and Kasa only work with their own separate app so I would have had to have two separate apps even though both were TP link. Never bought any more smart plugs.
I’ve got about six smart plugs that all stopped working because of lack of support. I am no longer interested in smart plugs.
Shelly makes devices that are compatible with ESPHome and Tasmota, solving this problem.
I feel like every article out there is missing this and keeps blaming Windows Update vs an update pushed to a specific piece of software by a third-party developer. I get end-users not understanding how things work but tech writers should be more knowledgeable about the subject they write about for a living.
Yeah, what? 3.1 not getting updates has nothing to do with this. Software developed for 3.1 can still be updated. This article is just silly.
It isn’t even a Windows update, but a software update.
deleted by creator
Likely the same reason why banks and other financial institutions still use COBOL and Fortran code written in the 1970s or earlier on archaic mainframes: Top management decided at some point it was too expensive to rewrite everything from scratch in some modern language for modern hardware, so they just limp along with what they have.
A 16-bit app written for Windows 3.x would almost certainly have to be rewritten for modern, 64-bit Windows.
While i figured the cost would be a factor, i just figured they were sticking with a system that works. If it serves their needs effectively and reliably, why change it?
Edit: answered my own question–it doesn’t work anymore, and that’s why it needs to be changed
Yeah what a badly written article, with awful takeaways.
I thought I was eating an onion… Nope.
Windows 3.1 didn’t have the BSOD. It just froze. I remember with Windows NT 4, when we first got the BSOD, being so grateful that Microsoft decided to actually tell us that our computer wasn’t going to recover from the error. Otherwise, we’d just be sitting there, waiting, hoping it would unfreeze itself.
It never did
😄it still do that on my over 20y old 2gig RAM Arch KDE on wayland macBookPro 🤔
Windows 3.1 absolutely did have a BSoD, and as the other person mentioned, sometimes you could press a key and the OS would recover. More often than not you needed to reboot, though. Our family PC would BSoD all the damn time, and I had to put up with it throughout a good portion of my early childhood until my dad finally bought a Windows 98 SE PC. But that OS also had its fair share of instability issues. The “illegal operation” error message was a near-daily occurance.
It wasn’t until we got our first NT-based machine (XP) that we stopped having constant issues with Windows. The DOS-based Windows OSes were notoriously unstable.
I think that NT 3.51 had a blue screen of death
Windows 3.1 did have a BSOD. It wasn’t always fatal, you could try to hit enter to go back to Windows, but most of the time it wasn’t really recoverable, Windows often wouldn’t work right afterwards.
I ran into them all the time in 3.11 on our 486 which had some faulty RAM (the BSOD would even be scrambled). If we could get back to Windows after that, it’d just be in a zombie state where moving the mouse around would paint stuff over whatever was left on screen, and wouldn’t respond to clicks or keypresses.
Fun times.
IIRC Windows 95 did that as well
Are you sure? I remember a long time ago being able to trigger a BSOD by opening Windows Calculator and dividing any number by 0. And I’m pretty sure that was 3.1 or 3.11.
In fact, I remember being able to change the color of the BSOD.
As another user mentioned, the BSOD first came in Windows NT 3.51.
But it definitely wasn’t in Windows 3.1 or Windows 3.11
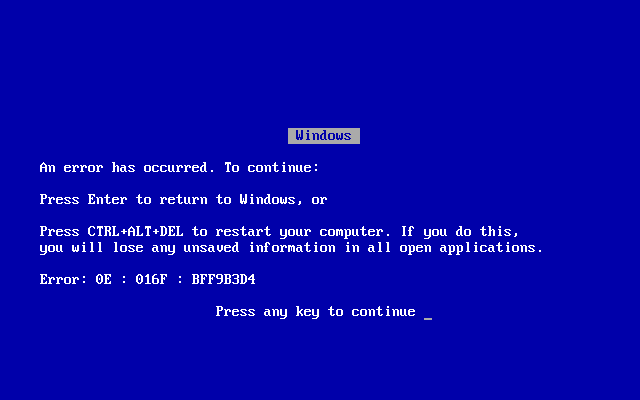
The other user is wrong. I clearly remember the BSoD in Windows 3.1. You can find it easily with a simple web search. Here it is:
Hell, there were even memes of it:
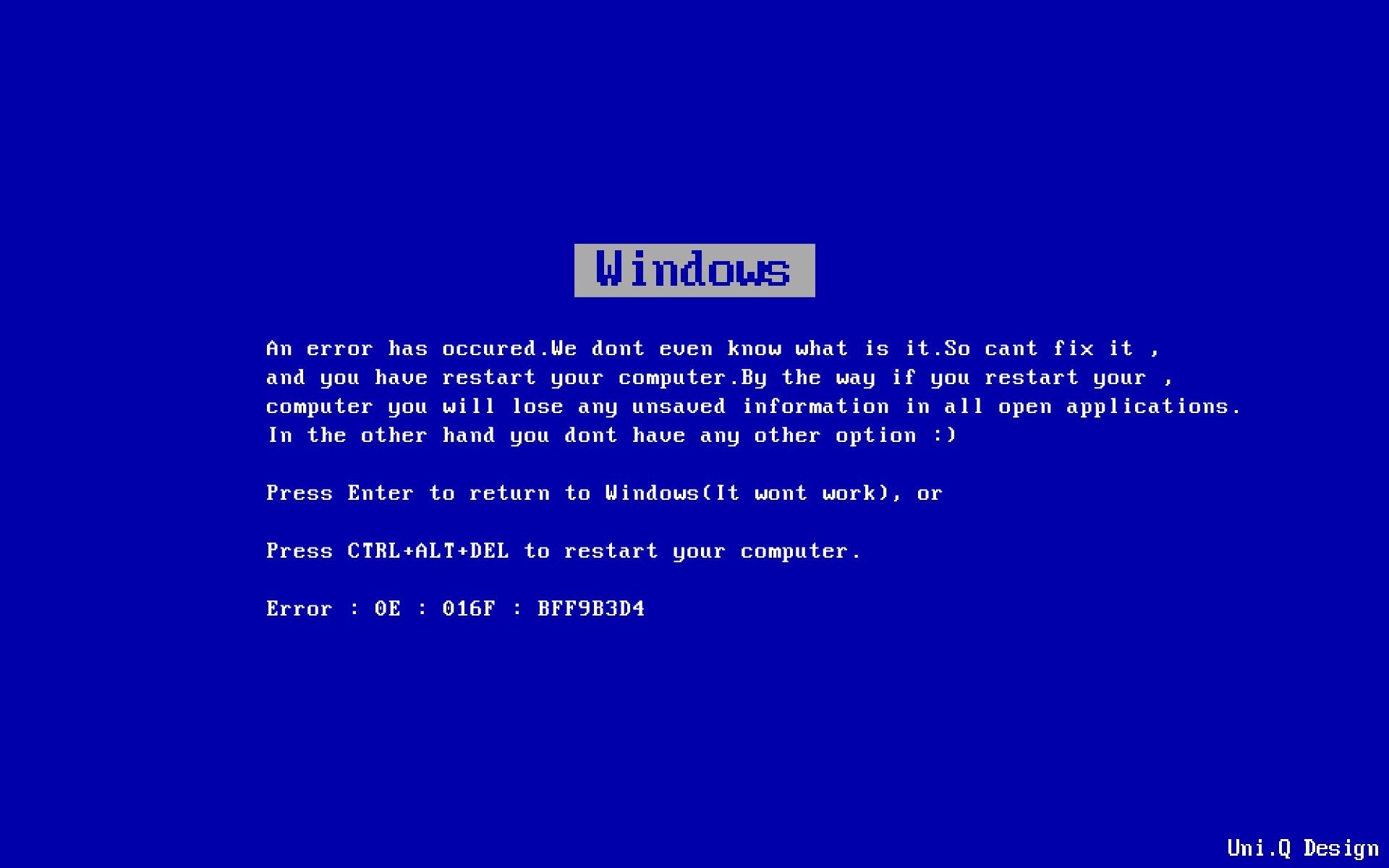
🤯
I thought everyone already switched to 3.11
Everything we know about this is that it was a disaster waiting to happen. Why the heck aren’t the airlines using Linux instead of Windows for critical stuff? How about something like…Chrome OS? Then you don’t need CrowdStrike because your OS is already secure because of the built in VMs and because it is Linux. Pay google for support and no updates unless there is something critical.
Mainly people are down voting you because Linux had also been affected by Crowdstrike before. Only a few months ago at that. There aren’t any more defenses in Linux systems against this kind of problem than there are in Windows ones. This isn’t even strictly speaking a security issue either. It’s more like a bug in critical software that just happens to be security related. It’s a bit like when that Grub update broke some people’s arch setups.
It’s not that Linux can’t have security problems. I still remember the very first internet virus in 1987 that traveled thru Unix machines. But Windows is the worst OS for critical systems precisely because it is the most common OS. Anything is better than windows. Linux, MacOS, or even an old IBM mainframe OS and those awful tn3270 terminals. Also, Chrome OS in particular has VMs instead of other VMs. It really is designed to be much more secure than Windows.
It’s more like a bug in critical software that just happens to be security related.
And so the cure is the same as the disease. Or actually worse in this case. The very fact that systems were constantly updated was itself the problem rather than the solution to the problem. How did nobody realize this was going to happen sooner or later?
Linux had also been affected by Crowdstrike before.
I’m guessing Crowdstrike issues a lot more Windows updates than Linux updates?
I’m guessing Crowdstrike issues a lot more Windows updates than Linux updates?
Not really. Linux is used for critical servers everywhere. No reason to update it less often.
It’s not that Linux can’t have security problems. I still remember the very first internet virus in 1987 that traveled thru Unix machines. But Windows is the worst OS for critical systems precisely because it is the most common OS. Anything is better than windows. Linux, MacOS, or even an old IBM mainframe OS and those awful tn3270 terminals. Also, Chrome OS in particular has VMs instead of other VMs. It really is designed to be much more secure than Windows
This isn’t a hacking attempt. It’s not a security breach. None of the “Windows is more common” stuff is actually valid in this case. The fact it’s not actually true is even more funny. When it comes to servers and smartphones, and the total number of devices in general, Linux outnumbers Windows. Linux isn’t actually niche in the slightest, only purists running Arch or Ubuntu think that because they ignore any Linux they don’t like, like Android.
You also don’t understand anything about ChromeOS security either. They don’t use VMs for system security. Early Chromebooks actually had virtualization disabled! Sandboxing and virtualization aren’t the same thing. The reason it’s secure is largely because it can’t do anything, it uses an a/b root system, and it has secure boot by default. It’s not that fancy anymore.
Chrome the web browser also has sandboxing on Windows, and modern Windows uses secure boot. Edge and Chrome have the same foundation btw. What it’s missing is the immutable a/b root system, and the fact Windows allows running arbitrary executables when ChromeOS doesn’t. There are actually tools for making Windows immutable, and with group policy or things like S mode you can restrict who can run what executables. Meaning with the right settings it’s almost as secure as ChromeOS. Even more funny Windows actually does use virtualization based security. So you have that backwards too.
Stop talking about shit you don’t understand and learn about it instead.
This isn’t a hacking attempt.
No but it is the result of trying to stop hacking attempts.
They don’t use VMs for system security.
They do. A major reason they use them is to make ChromeOS way more secure than windows.
Linux isn’t actually niche in the slightest
It’s fragmented. There is no single version
Stop talking about shit you don’t understand and learn about it instead.
Stop being a jackass and learn to communicate in civilized fashion.
with group policy or things like S mode you can restrict who can run what executables.
Companies don’t run windows in S mode and every OS has group security.
None of the “Windows is more common” stuff is actually valid in this case.
When I learned that companies are actually letting Cloudstrike download the equivalent of KERNAL MODE code into their critical systems I was dumbfounded. Who could have possibly thought that was a good idea? This was absolutely a disaster that was just waiting to happen.
However, if it happened on Linux, it could have been immediately bypassed.
Automatically reverting the kernel wouldn’t do anything as the kernel nor the module Crowdstrike uses were updated. Rather the file the module reads was updated and replaced with a corrupted version that causes the module to crash when it tries to read it.
There is a great video explaining the basics of what happened here: https://youtu.be/wAzEJxOo1ts?si=_agkbdBHJnhQmbdP
Microsoft already have a mechanism to disable problematic modules on next boot. Problem being that Crowdstrike registers itself as an essential driver, as they don’t want the system to boot without it for security reasons.
You keep saying Chrome OS uses VMs for security. Unless something has seriously changed since I last read up on their security mechanisms they don’t. Maybe something has changed. Do you have any evidence? If not you’re just talking out of your arse.
Sure I’ve got lots of evidence.
https://www.security.org/antivirus/chromebooks/
[There’s no question that, when it comes to viruses and other forms of malware, Chromebooks are safe. How safe? Well, the website CVE Details1 lists just 55 vulnerabilities for Chrome OS. Compare that to 1,111 vulnerabilities for Windows 10, and a whopping 2,212 for Mac’s OS X; with five percent as many vulnerabilities as its closest competitor, it’s a pretty simple matter to declare Chromebook the safest option…there’s no question that Chromebooks are among the most secure computers you can buy]
55 vulnerabiilites for Chrome OS vs 1111 vulnerabilities for Windows. Huge difference.
Rather the file the module reads was updated and replaced with a corrupted version that causes the module to crash when it tries to read it.
Yes it was a ridiculous system to have kernel mode code on the filesystem. Even if a bad pointer didn’t crash the system a hacker could have put in their own code. And yes such a terrible security system would have affected Linux too. But with ChromeOS, the system is already secure. No need to use a terrible security system like Cloudstrike in the first place.
No you don’t have any evidence at all. You were specifically speaking about Chrome OS using VMs inside VMs. That article doesn’t mention VMs once.
I never once disputed that it was more secure than an average Windows installation, because frankly that’s obvious. What you don’t seem to understand is what can be done to lock down modern Windows and Linux systems.
Yes it was a ridiculous system to have kernel mode code on the filesystem. Even if a bad pointer didn’t crash the system a hacker could have put in their own code. And yes such a terrible security system would have affected Linux too. But with ChromeOS, the system is already secure. No need to use a terrible security system like Cloudstrike in the first place.
For one the same article you are referencing talks about using anti-malware on ChromeOS as Chrome OS isn’t malware proof. Though I don’t think it’s possible for Chrome OS to break so badly from one of these products.
ChromeOS though isn’t actually suitable for running servers like Windows and Linux are. It can’t do nearly the same number of things. It’s a bit like comparing a knife to a safety razor. One is safer for shaving sure, however the other one can be used for cooking, hunting, wood work, etc.
Second all kernel mode code lives on the filesystem. How did you think it worked? On Linux and Windows the kernel itself needs storing somewhere, as do the modules.
You keep showing me again and again that you don’t understand the world of computers and modern IT infrastructure. Do you even have any qualifications or work experience in IT?
Edit: I actually did some research myself. ChromeOS can use a Virtual Machine to run Linux software, but not in it’s default configuration. There is also none of this VMs inside VMs stuff you were talking about. If you want to see virtualization really put to work look at a modern server setup or something like Qubes OS.
The disaster likely happened because Crowdstrike didn’t do any phased rollouts or testing, which would have picked up a glitch like these before it could brick countless millions of systems. Blaming Microsoft for what is most likely gross negligence from a major cybersecurity firm is downright disingenuous.
Also, recommending an overglorified web browser baked into an OS which can only run web and Android applications to run critical infrastructure is downright laughable, ESPECIALLY when Google are known for their downright nonexistent customer support.
People use Windows because it’s the most well-known and used OS on the market, and because Microsoft is a multi-billion dollar tech giant with a dedicated customer support and tech team to fix issues posthaste.
blaming Microsoft
I’m not blaming Microsoft. I am blaming companies for using Microsoft for critical systems.
Also, recommending an overglorified web browser baked into an OS which can only run web and Android applications to run critical infrastructure is downright laughable,
You not understanding that ChromeOS is a highly secure Linux computer is that can run any Linux program is downright laughable ignorance.
ESPECIALLY when Google are known for their downright nonexistent customer support.
Their software is way too widely used to provide you with free customer support. Microsoft is no different.
I’m inclined to believe this post, claiming this article is BS https://mastodon.social/@jplebreton/112825798853315264
Yes, the update bricked the systems, meaning the software that powers their business was unaccessible, reinstalling any version of windows would not restore the software built on top of the os. Thus why it became a huge ordeal rather than a simple update push from Microsoft, a bricked system can’t receive a fix remotely.
Hang on, if you’re using CrowdStrike but not getting the updates, then why are you using it at all?
Because none of these journalists have a basic understanding of what actually happened lol
Is this actually confirmed anywhere though? I keep seeing it repeated and the only ‘source’ is a ?xeet? .
Same, I’m pretty sure it’s not true.
Ahhhh, the Technology Trap. The modern world has become a mere handful of bad zeros away from having this house of cards crash down and kill almost everyone.
Technology is great and makes our modern society comfy and great. But it also can be the Sword of Damocles. When will that slender thread break and kill us all?












